WELCOME
2010年1月28日 星期四
TuneXP 1.5
Although it might be a bit too technical for average folks, this tiny, free utility nonetheless offers a helpful set of optimization tools for more advanced users of Windows XP. TuneXP's interface is certainly no beauty, but since all of its tools are accessible via menu items, it's simple enough to operate. The Memory and File System section lets you perform tweaks such as accelerating DLL unloading and defraging boot files. The other system tools are organized into categories such as Internet, Hardware, and Services. While many of the program's features will go over the heads of those who aren't technically inclined, we're glad the help files fully explain what each part of the program does. Best of all, TuneXP is totally free, making it a fine pick for those who suspect their OS could be in better shape than it currently is.
2010年1月26日 星期二
A free registry defragmentation and cleanup tool, simple to use, safe and reliable.
Description
WinMend Registry Defrag is a free registry defragmentation and cleanup tool. It can rebuild registry index safely and clear waste registry space to make it easy for Windows and other applications to find data more efficiently. As Windows registry is re-organized, you will enjoy much improved operating system performance. This tool is safe, reliable, and simple to understand and use. You will be reminded to reboot your computer and installation.Features
-
 1. Safe and Reliable
1. Safe and Reliable
We utilized Microsoft’s latest base level reconstruction technology in this software. Based on numerous limit tests performed on WinMend Registry Defrag, we guarantee the maximum safety of you Windows operating system once the registry is rebuilt. -
 2. Intelligent Recommendation
2. Intelligent Recommendation
Some settings in Windows system are not suitable for defragmentation. Forced defragmentation may cause serious instability to your system. With unique intelligent filter technology, WinMend Registry Defrag can accurately identify the settings not suitable for defragmentation, prompt the user and stop the defragmentation. -
 3. Fast Running
3. Fast Running
While we consider system safety our primary goal, we don’t compromise our speed. WinMend Registry Defrag runs 30% faster than similar products. Registry defragmentation can be completed within 2 minutes for most Windows systems. -
 4. Wizard-Based Operation
4. Wizard-Based Operation
Our wizard-based design enables even an entry level user to complete defragmentation with ease. The task requires really just a few clicks! -
 5. Colorful Skins and Full Compatibility with Microsoft Operating Systems
5. Colorful Skins and Full Compatibility with Microsoft Operating Systems
Interfaces of 5 different colors are available in all WinMend applications. You can switch to a favorite one at any time to prevent visual fatigue. All applications fully support Windows 2000/XP/Vista/7 (32-bit and 64-bit) operating systems.
MagicISO Virtual CD/DVD-ROM Overview
MagicISO Virtual CD/DVD-ROM Overview
You are here: Tutorials > MagicISO Virtual CD/DVD-ROM(MagicDisc) Overview
View History
MagicDisc is freeware. It is very helpful utility designed for creating and managing virtual CD drives and CD/DVD discs. For anyone who deals with CD-based programs – it is a MUST. MagicDisc allows you to use almost all CD/DVD image without burning them onto CD or DVD in order to easily access your favorite games, music, or software programs ---- It works like a real CD/DVD-ROM: You can run programs, play games, or listen to music from your virtual CD-ROM. Allowing you to run your game images at over 200x faster than from a conventional CD/DVD-ROM. MagicDisc is a powerful utility that uses a unique combination of options to ensure a perfect back-up every time. Partner with MagicISO, Your original games/program discs can be safely stored away, MagicISO mean that you always have your expensive media stored safely as CD/DVD image file on your hard drive, and use them with MagicDisc just like using the original discs. At the office: Program discs and many other applications generally require the original disc to be in the computer's CD-ROM drive. This restricts the amount of people in your office who can have access to the same software at the same time without the cost of additional discs. MagicDisc virtual drives resolve that problem for you. No more hunting around the offices for that elusive disc you need to run your application, everything you require is just a click away.
Change display language in Windows editions (Vista & 7)
Did you buy a Windows laptop from abroad and want it to talk to you in your mother tongue?
Try Vistalizator - this tool allows you to change display language in Windows editions other than (officially supported) Ultimate, like Starter, Home Basic, Home Premium and Business/Professional.
Vistalizator overrides the limit of one MUI language on non-Ultimate Windows editions.
See details about using multiple languages in Windows.
Try Vistalizator - this tool allows you to change display language in Windows editions other than (officially supported) Ultimate, like Starter, Home Basic, Home Premium and Business/Professional.
Vistalizator overrides the limit of one MUI language on non-Ultimate Windows editions.
See details about using multiple languages in Windows.
Features
- Works in 32-bit and 64-bit Windows Vista/Windows 7
- Change Windows display language in less than 5 minutes! (Express installation mode)
- Uses official Microsoft Windows language packs
- You can install all 36 MUI languages and switch between them easily
- You can install 55 Vista LIP languages on top of specific MUI languages
- Compatible with Vista Service Pack 1 and Vista Service Pack 2
- User Account Control (UAC) compliant - prompts for administrative privileges
- Windows Speech Recognition works with all supported languages:
Chinese, English, French, German, Japanese and Spanish - Languages can be installed either in Internal or in Express mode, see details
Multiple languages in Windows
To be able to use different/multiple MUI display languages:- You are the lucky user of Windows Ultimate/Enterprise
- Upgrade your edition to Ultimate - purchase a Windows Anytime Upgrade
- Get a Windows installation DVD in different language and do a clean install of Windows
(you can use Windows Easy Transfer for all your data and settings) - Make your own Multilanguage Vista DVD and do a clean install of Vista
- Use Vistalizator in Windows Vista or Windows 7 and install languages in a few minutes
2010年1月24日 星期日
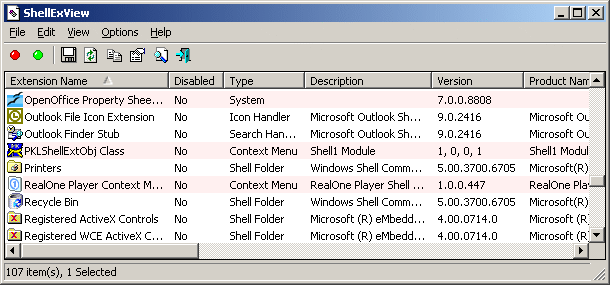
ShellExView v1.45 - Shell Extensions Manager
Description
Shell Extensions are in-process COM objects which extends the abilities of Windows operating system. Most shell extensions are automatically installed by the operating system, but there are also many other applications that install additional shell extension components. For example: If you install WinZip on your computer, you'll see a special WinZip menu when you right-click on a Zip file. This menu is created by adding a shell extension to the system. The ShellExView utility displays the details of shell extensions installed on your computer, and allows you to easily disable and enable each shell extension.ShellExView can be used for solving context-menu problems in Explorer environment. For more information, read the following article: Right-click is slow or weird behavior caused by context menu handlers
EASEUS Data Recovery Wizard 4.3.6
Do you want to recover your important files today for free? Free download the full version of EASEUS Data Recovery Wizard – The professional data recovery software to recover your lost data for Windows 2000/2003/XP/Vista!
EASEUS Data Recovery Wizard is an advanced Data Recovery Software to Format Recovery, Partition Recovery, and Recover Deleted Files emptied from the Recycle Bin or restore data lost due to software crash, virus attack, etc. It offers users with quick scan, easy and safe data
recovery.
Features:
Recover deleted or lost files emptied from the Recycle Bin.
File recovery after accidental format, even if you have reinstalled Windows.
Get data back from RAW hard drives.
Get back files after a partitioning error.
Disk recovery after a hard disk crash.
Recover office documents, photos, images, videos, music, email, etc.
Support FAT12, FAT16, FAT32, NTFS/NTFS5 file systems.
EASEUS Data Recovery Wizard is an advanced Data Recovery Software to Format Recovery, Partition Recovery, and Recover Deleted Files emptied from the Recycle Bin or restore data lost due to software crash, virus attack, etc. It offers users with quick scan, easy and safe data
recovery.
Features:
Recover deleted or lost files emptied from the Recycle Bin.
File recovery after accidental format, even if you have reinstalled Windows.
Get data back from RAW hard drives.
Get back files after a partitioning error.
Disk recovery after a hard disk crash.
Recover office documents, photos, images, videos, music, email, etc.
Support FAT12, FAT16, FAT32, NTFS/NTFS5 file systems.
2010年1月22日 星期五
PowerShell的R2上安裝服務器核心
It's here!就在這裡! PowerShell for Server Core. PowerShell中的服務器核心。 This is just a quick lesson in how to install it.這僅僅是一個快速汲取教訓,如何安裝它。 So, how do you get it?那麼,你如何得到它?
Once you get Windows Server 2008 Core R2 installed, Type OCLIST .一旦你的Windows Server 2008核心R2的安裝類型OCLIST。 We need to make sure that the following is installed:我們必須確保以下安裝:
• NetFx2-ServerCore (There may be additional characters after this) •NetFx2 - ServerCore(可能有其他字符之後)
• MicrosoftWindowsPowerShell •MicrosoftWindowsPowerShell
If you are missing any of these two, install them with the instructions below.如果你缺少其中任何兩個,安裝它們與下面的說明。 Don't forget, these are case sensitive.不要忘記,這些都是大小寫敏感的。
For NetFx2-ServerCore對於NetFx2 - ServerCore
OCSetup NetFX2-ServerCore OCSetup NetFX2 - ServerCore
OCSetup NetFX2-ServerCore OCSetup NetFX2 - ServerCore
For MicrosoftWindowsPowerShell對於MicrosoftWindowsPowerShell
OCSetup MicrosoftWindowsPowerShell OCSetup MicrosoftWindowsPowerShell
OK, now that the software is installed, navigate to c:\Windows\System32\WIndowsPowerShell\V1.0 .好了,現在該軟件安裝,瀏覽到c:\窗口\ System32 \ WIndowsPowerShell \ 1.0。 Once there, type PowerShell you will notice that the prompt changes to PS .一旦輸入PowerShell中你會發現提示更改為私人秘書 。 Go ahead and type Get-Command and press Enter If this worked, PowerShell is installed.請繼續和類型同享命令 ,然後按 Enter如果此工作,PowerShell安裝。 It is not going to be the pretty blue window, but inside the command prompt.這不會是漂亮的藍色窗口,但裡面的命令提示符。 Go ahead and type Write-Host –fore blue “Hello World” and press Enter .請繼續和類型寫主機脫穎而出藍色的“Hello World”並按下回車鍵 。 You will see the text change color.您將看到文本改變顏色。 The color formatting will allow you to make your scripts in Server Core look pretty.顏色格式將允許您使您的腳本在服務器核心好看。 Typing Exit will take you back to the command prompt. 鍵入 exit將帶你回到命令提示符。
OCSetup MicrosoftWindowsPowerShell OCSetup MicrosoftWindowsPowerShell
OK, now that the software is installed, navigate to c:\Windows\System32\WIndowsPowerShell\V1.0 .好了,現在該軟件安裝,瀏覽到c:\窗口\ System32 \ WIndowsPowerShell \ 1.0。 Once there, type PowerShell you will notice that the prompt changes to PS .一旦輸入PowerShell中你會發現提示更改為私人秘書 。 Go ahead and type Get-Command and press Enter If this worked, PowerShell is installed.請繼續和類型同享命令 ,然後按 Enter如果此工作,PowerShell安裝。 It is not going to be the pretty blue window, but inside the command prompt.這不會是漂亮的藍色窗口,但裡面的命令提示符。 Go ahead and type Write-Host –fore blue “Hello World” and press Enter .請繼續和類型寫主機脫穎而出藍色的“Hello World”並按下回車鍵 。 You will see the text change color.您將看到文本改變顏色。 The color formatting will allow you to make your scripts in Server Core look pretty.顏色格式將允許您使您的腳本在服務器核心好看。 Typing Exit will take you back to the command prompt. 鍵入 exit將帶你回到命令提示符。
VMC to Hyper-V Import Tool Available
VMC to Hyper-V Import Tool
Now that we have launched the Microsoft Virtualization strategy this Monday, I wanted to release my tool so people could start using it to import their old Virtual Machine configurations. So first of all, what is the VMC to Hyper-V Import Tool and what was it intended for?
The tool
VMC to Hyper-V Import Tool, VMC2HV for short, imports the configuration from a Virtual Machine Configuration (VMC) file. Both Virtual PC and Virtual Server use VMC files to store the hardware and other properties of a VM. It reads the VMC file and maps all relevant properties to those for a Hyper-V VM. For those properties that did not exist, it provides additional options. Those properties that no longer exist are ignored.
VMC2HV was developed to ease the transition from Virtual Server to Hyper-V. As I explained in an earlier post, I was quite annoyed by the fact that I had to enter all hardware properties manually if I wanted to use the VHD files from the Virtual Server VM with the hardware settings as they were in the original VM. It really took a lot of time to get my VS VM’s under Hyper-V. So I did not want to do that again and decided to develop a tool that would import the properties for me (development of the tool took quite more time but it was fun…).
Scope
The scope of the tool was initially to import Virtual Server VMC files. But some people also wanted to be able to import Virtual PC VMC files. So I did some additional testing with Virtual PC 2007 VMC files. It was not extensive but I did modify the code in several places to accommodate the differences between Virtual PC and Virtual Server. I did not specifically test Virtual PC 2004 VMC files. I imported several and it worked but I didn’t test those VMC files since the product has been superseded long ago. Basically the same is true for Virtual Server 2005 R2 SP1. I only tested VMC files under the latest release of Virtual Server 2005.
Out of scope
The tool imports a VM configuration. This means it does nothing inside the VM like removing Virtual Machine Additions or installing Integration Components. I just want to make that clear to manage the expectations. Although uninstalling the Additions, installing the Integration Components and the process involved requires some work it is much less than reading the VMC file and searching and copying the hardware properties over to Hyper-V. If you want automatic removal of Additions and installation of Integration Components, use System Center Virtual Machine Manager (SCVMM) 2008.
Comparison with SCVMM
VMC2HV was never developed to replace the SCVMM functionality, as VMRCplus was never developed for the same reason. SCVMM is an enterprise class product which you should use to import, create and manage virtual machines. SCVMM can import the VMC file as well and provides some additional management functionality. VMC2HV basically does the same but was intended for people who do not (yet) have SCVMM. For example all people using Hyper-V on laptops or a couple of servers. Using SCVMM just for importing VMC files would be a bit too much of a step.
Features
So what does the tool offer? In a list of features:
· Import of VMC files of both VS2005 and VPC2007
· Creation of VM on local Hyper-V host
· Creation of VM on remote Hyper-V host
· Validation of virtual disk and ISO files in local scenario
· Editing of virtual drive image paths (vhd, vfd, iso)
· Swapping of the first SCSI disk with the first IDE disk
· Specification of static MAC addresses
· Specification of either legacy (emulated) or enhanced network adapter
· Specification of # of virtual processors and resource control
· Specification of management settings
· Specification of COM ports
· Specification of device boot order
· Specification of alternate Virtual Machine path
· Built-in help in CHM file
· Support for both x86 and x64 Vista and Server 2008
As you can see, VMC2HV not only imports the configuration but lets you adjust almost any setting before creating the VM in Hyper-V. Several shortcut keys have been added to help speed the process if you only want to do an import-and-create of many VMC files.
Requirements
You can import VMC files from any file location. Then you can create the VM either locally or remotely. In the remote scenario, both the client where VMC2HV runs and the remote Hyper-V host must be in the same domain. Or alternatively, both client and remote Hyper-V host can exist in a workgroup but you need to use mirrored administrator accounts (both same administrator, same password). Other configurations simply do not work.
The tool prevents importing VMC files which contain either saved state information or Undo disks. VM’s must be shut down and Undo disks must be committed or discarded.
Support
I hope it just works for you but I know there are always circumstances I did or could not test. If you run into issues with a VMC file, send me the file and I may look at it to see what causes problems. If the VMC file is from an old Virtual PC version, I prefer you open the VMC file in Virtual PC 2007 SP1 and save the configuration from there. It will be reformatted in Virtual PC 2007 layout and likely to solve any import issues. If you cannot, I can look into the specific issue. The same applies to old Virtual Server VMC file versions. If import fails when using the latest VMC files, send a copy to me.
Before submitting any issues, please press F1 and see if your question is addressed in the help file. As the license agreement states, I may not support an issue at all or may not have the time. I will support on a best-effort basis.
Download
You can find both the x86 and x64 files here.
2010年1月21日 星期四
LockHunter is a foolproof file unlocker
Key Features
- Shows processes locking a file or folder
- Allows to unlock, delete, copy or rename a locked file
- Allows to kill locking process
- Allows to remove locking processes from hard drive
- Integrates in to Explorer menu
- It deletes files into the recycle bin, so you may restore them if deleted by mistake
- Supports both 32 and 64bit Windows
 See More Screenshots! |
Download Size: ~1.2 MB, OS: Windows 2000, XP, 2003, Vista, 7 |
Install the Windows Server Backup Feature on Server Core
Before you can back up a Server Core computer, you must install the Windows Server Backup feature. This can be done in two ways:
From the Command Line
Using Ocsetup.exe, you can install the Windows Server Backup feature with the following command:
C:\Users\Administrator.FABRIKAM>start /w ocsetup WindowsServerBackup
To verify the result, you can use this:
C:\Users\Administrator.FABRIKAM>oclist | find " Installed"
Using an Answer File
You can also install the Windows Server Backup feature using an answer file. To do so, simply perform the following steps:
1. Begin by creating and configuring an answer file for unattended installation of Server Core. For information on how to do this, see Chapter 2, “Deploying Server Core.”
2. On your technician computer, open your answer file in Windows System Image Manager (Windows SIM).
3. In the Windows Image pane, expand the Packages node to display the nodes beneath it. Expand the Foundation node to display the Microsoft-Windows-ServerCore-Package node beneath that. Then right-click the address Microsoft-Windows-ServerCore-Package node and select Add To Answer File. The Microsoft-Windows-ServerCore-Package should now be selected in the Answer File pane.
- From the command line, using the Ocsetup command
- By using an answer file during an unattended installation of Server Core
Using Ocsetup.exe, you can install the Windows Server Backup feature with the following command:
C:\Users\Administrator.FABRIKAM>start /w ocsetup WindowsServerBackup
To verify the result, you can use this:
C:\Users\Administrator.FABRIKAM>oclist | find " Installed"
Tips RSS Feed
Subscribe to the TechNet Magazine Tips RSS feed.
You can also install the Windows Server Backup feature using an answer file. To do so, simply perform the following steps:
1. Begin by creating and configuring an answer file for unattended installation of Server Core. For information on how to do this, see Chapter 2, “Deploying Server Core.”
2. On your technician computer, open your answer file in Windows System Image Manager (Windows SIM).
3. In the Windows Image pane, expand the Packages node to display the nodes beneath it. Expand the Foundation node to display the Microsoft-Windows-ServerCore-Package node beneath that. Then right-click the address Microsoft-Windows-ServerCore-Package node and select Add To Answer File. The Microsoft-Windows-ServerCore-Package should now be selected in the Answer File pane.
2010年1月17日 星期日
Android Apps(鈴聲~錄音~剪接~)
- Ringdroid
-
- Open an existing audio file
- View a scrollable waveform representation of the audio file at 5 zoom levels
- Set starting and ending points for a clip within the audio file, using an optional touch interface
- Play the selected portion of the audio, including an indicator cursor and autoscrolling of the waveform
- Play anywhere else by tapping the screen
- Save the clipped audio as a new audio file and mark it as Music, Ringtone, Alarm, or Notification.
- Record a new audio clip to edit
- Delete audio (with confirmation alert)
- Launches automatically in response to the GET_CONTENT intent with a mime type of audio/ if any other application wants to pick an audio file - for example the "Rings Extended" application.
- Assign a ringtone directly to a contact.
FuturixImager “S” (Picture edit tools)
FuturixImager “S” Beta 2
My first release of the new decade is a second beta of sixth generation of FuturixImagerDownload now! (2.72 MB)
The main focus of this version is improvement of file format registration* – now supporting “Default Programs” for the recent versions of Windows (7, Vista, 2008) and also with improved registration for XP (now it does not require administrative privileges).
* – individual icons for different formats are not here yet, but they will be added soon.
Copy正版CD
Details
HandBrake is an open-source, GPL-licensed, multiplatform, multithreaded video transcoder, available for MacOS X, Linux and Windows.Screenshots
Supported Sources:
- Any DVD-like source: VIDEO_TS folder, DVD image or real DVD (unencrypted--protection methods including CSS are not supported internally and must be handled externally with third-party software and libraries), and some .VOB and .TS files
- Most any multimedia file it can get libavformat to read and libavcodec to decode.
Outputs:
- File format: MP4 and MKV
- Video: MPEG-4, H.264, or Theora
- Audio: AAC, CoreAudio AAC (OS X Only), MP3, or Vorbis. AC-3 pass-through, DTS pass-thorugh (MKV only)
Misc features:
- Chapter selection
- Subtitles
- Integrated bitrate calculator
- Picture deinterlacing, cropping and scaling
- Live Video Preivew
Credits
HandBrake uses a lot of (L)GPL librairies from the Linux world: HereThank their authors!
2010年1月14日 星期四
Exchange 2007 Queue filling up with blank senders
http://msexchangeteam.com/application servers to relay off Exchange Server 2007 )
http://msexchangeteam.com
http://support.microsoft.cAnti Spam Agents on Exchange 2007)
http://www.petri.co.il/red
http://msexchangeteam.com
http://support.microsoft.c
http://www.petri.co.il/red
Allowing application servers to relay off Exchange Server 2007
From time to time, you need to allow an application server to relay off of your Exchange server. You might need to do this if you have a SharePoint, a CRM application like Dynamics, or a web site that sends emails to your employees or customers.
You might need to do this if you are getting the SMTP error message "550 5.7.1 Unable to relay"
The top rule is that you want to keep relay restricted as tightly as possible, even on servers that are not connected to the Internet. Usually this is done with authentication and/or restricting by IP address. Exchange 2003 provides the following relay restrictions on the SMTP VS:

Here are the equivalent options for how to configure this in Exchange 2007.
Allow all computers which successfully authenticate to relay, regardless of the list above
Like its predecessor, Exchange 2007 is configured to accept and relay email from hosts that authenticate by default. Both the "Default" and "Client" receive connectors are configured this way out of the box. Authenticating is the simplest method to submit messages, and preferred in many cases.
The Permissions Group that allows authenticated users to submit and relay is the "ExchangeUsers" group. The permissions that are granted with this permissions group are:
Only the list below (specify IP address)
This option is for those who cannot authenticate with Exchange. The most common example of this is an application server that needs to be able to relay messages through Exchange.
First, start with a new custom receive connector. You can think of receive connectors as protocol listeners. The closest equivalent to Exchange 2003 is an SMTP Virtual Server. You must create a new one because you will want to scope the remote IP Address(es) that you will allow.

The next screen you must pay particular attention to is the "Remote Network settings". This is where you will specify the IP ranges of servers that will be allowed to submit mail. You definitely want to restrict this range down as much as you can. In this case, I want my two web servers, 192.168.2.55 & 192.168.2.56 to be allowed to relay.

The next step is to create the connector, and open the properties. Now you have two options, which I will present. The first option will probably be the most common.
Option 1: Make your new scoped connector an Externally Secured connector
This option is the most common option, and preferred in most situations where the application that is submitting will be submitting email to your internal users as well as relaying to the outside world.
Before you can perform this step, it is required that you enable the Exchange Servers permission group. Once in the properties, go to the Permissions Groups tab and select Exchange servers.

Next, continue to the authentication mechanisms page and add the "Externally secured" mechanism. What this means is that you have complete trust that the previously designated IP addresses will be trusted by your organization.

Caveat: If you do not perform these two steps in order, the GUI blocks you from continuing.
Do not use this setting lightly. You will be granting several rights including the ability to send on behalf of users in your organization, the ability to ResolveP2 (that is, make it so that the messages appear to be sent from within the organization rather than anonymously), bypass anti-spam, and bypass size limits. The default "Externally Secured" permissions are as follows:
Option 2: Grant the relay permission to Anonymous on your new scoped connector
This option grants the minimum amount of required privileges to the submitting application.
Taking the new scoped connector that you created, you have another option. You can simply grant the ms-Exch-SMTP-Accept-Any-Recipient permission to the anonymous account. Do this by first adding the Anonymous Permissions Group to the connector.

This grants the most common permissions to the anonymous account, but it does not grant the relay permission. This step must be done through the Exchange shell:
Although it is completely different from the Exchange 2003 way of doing things, hopefully you find the new SMTP permissions model to be sensible.
More information
See the following for more information:
You might need to do this if you are getting the SMTP error message "550 5.7.1 Unable to relay"
The top rule is that you want to keep relay restricted as tightly as possible, even on servers that are not connected to the Internet. Usually this is done with authentication and/or restricting by IP address. Exchange 2003 provides the following relay restrictions on the SMTP VS:

Here are the equivalent options for how to configure this in Exchange 2007.
Allow all computers which successfully authenticate to relay, regardless of the list above
Like its predecessor, Exchange 2007 is configured to accept and relay email from hosts that authenticate by default. Both the "Default" and "Client" receive connectors are configured this way out of the box. Authenticating is the simplest method to submit messages, and preferred in many cases.
The Permissions Group that allows authenticated users to submit and relay is the "ExchangeUsers" group. The permissions that are granted with this permissions group are:
NT AUTHORITY\Authenticated Users {ms-Exch-SMTP-Submit}The specific ACL that controls relay is the ms-Exch-SMTP-Accept-Any-Recipient.
NT AUTHORITY\Authenticated Users {ms-Exch-Accept-Headers-Routing}
NT AUTHORITY\Authenticated Users {ms-Exch-Bypass-Anti-Spam}
NT AUTHORITY\Authenticated Users {ms-Exch-SMTP-Accept-Any-Recipient}
Only the list below (specify IP address)
This option is for those who cannot authenticate with Exchange. The most common example of this is an application server that needs to be able to relay messages through Exchange.
First, start with a new custom receive connector. You can think of receive connectors as protocol listeners. The closest equivalent to Exchange 2003 is an SMTP Virtual Server. You must create a new one because you will want to scope the remote IP Address(es) that you will allow.

The next screen you must pay particular attention to is the "Remote Network settings". This is where you will specify the IP ranges of servers that will be allowed to submit mail. You definitely want to restrict this range down as much as you can. In this case, I want my two web servers, 192.168.2.55 & 192.168.2.56 to be allowed to relay.

The next step is to create the connector, and open the properties. Now you have two options, which I will present. The first option will probably be the most common.
Option 1: Make your new scoped connector an Externally Secured connector
This option is the most common option, and preferred in most situations where the application that is submitting will be submitting email to your internal users as well as relaying to the outside world.
Before you can perform this step, it is required that you enable the Exchange Servers permission group. Once in the properties, go to the Permissions Groups tab and select Exchange servers.

Next, continue to the authentication mechanisms page and add the "Externally secured" mechanism. What this means is that you have complete trust that the previously designated IP addresses will be trusted by your organization.

Caveat: If you do not perform these two steps in order, the GUI blocks you from continuing.
Do not use this setting lightly. You will be granting several rights including the ability to send on behalf of users in your organization, the ability to ResolveP2 (that is, make it so that the messages appear to be sent from within the organization rather than anonymously), bypass anti-spam, and bypass size limits. The default "Externally Secured" permissions are as follows:
MS Exchange\Externally Secured Servers {ms-Exch-SMTP-Accept-Authoritative-Domain}Basically you are telling Exchange to ignore internal security checks because you trust these servers. The nice thing about this option is that it is simple and grants the common rights that most people probably want.
MS Exchange\Externally Secured Servers {ms-Exch-Bypass-Anti-Spam}
MS Exchange\Externally Secured Servers {ms-Exch-Bypass-Message-Size-Limit}
MS Exchange\Externally Secured Servers {ms-Exch-SMTP-Accept-Exch50}
MS Exchange\Externally Secured Servers {ms-Exch-Accept-Headers-Routing}
MS Exchange\Externally Secured Servers {ms-Exch-SMTP-Submit}
MS Exchange\Externally Secured Servers {ms-Exch-SMTP-Accept-Any-Recipient}
MS Exchange\Externally Secured Servers {ms-Exch-SMTP-Accept-Authentication-Flag}
MS Exchange\Externally Secured Servers {ms-Exch-SMTP-Accept-Any-Sender}
Option 2: Grant the relay permission to Anonymous on your new scoped connector
This option grants the minimum amount of required privileges to the submitting application.
Taking the new scoped connector that you created, you have another option. You can simply grant the ms-Exch-SMTP-Accept-Any-Recipient permission to the anonymous account. Do this by first adding the Anonymous Permissions Group to the connector.

This grants the most common permissions to the anonymous account, but it does not grant the relay permission. This step must be done through the Exchange shell:
Get-ReceiveConnector "CRM Application" | Add-ADPermission -User "NT AUTHORITY\ANONYMOUS LOGON" -ExtendedRights "ms-Exch-SMTP-Accept-Any-Recipient"In addition to being more difficult to complete, this step does not allow the anonymous account to bypass anti-spam, or ResolveP2.
Although it is completely different from the Exchange 2003 way of doing things, hopefully you find the new SMTP permissions model to be sensible.
More information
See the following for more information:
2010年1月13日 星期三
A reboot from a previous installation is pending.
重新啟動先前的安裝正在擱置
本主題的目的是要說明 Exchange Server Analyzer 工具所引出的特定問題。您只應將它套用到已執行過 Exchange Server Analyzer 工具且有遇到該特定問題的系統。Exchange Server Analyzer 工具可免費下載,它會從拓撲中的每台伺服器遠端收集組態資料,並自動分析該資料。產生的報告會詳述重要的組態問題、潛在問題及非預設的產品設定。遵循這些 建議,您便能達到較佳的效能、延展性、可靠性及執行時間。如需此工具的相關資訊或是要下載最新版本,請參閱 Microsoft Exchange Analyzer (http://go.microsoft.com/fwlink/?linkid=34707)。 主題上次修改日期: 2008-01-16
Microsoft Exchange Server 安裝程式無法繼續,因為重新啟動先前的安裝或更新正在擱置。
Exchange Server Analyzer 會讀取下列登錄機碼,以判定系統是否需要在安裝或移除軟體更新 (例如安全性更新、重大更新或 Hotfix) 之後重新啟動。
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Updates\UpdateExeVolatile
Exchange Analyzer 也會檢查下列登錄機碼,以判定先前安裝的軟體更新是否未完成,且系統是否必須重新啟動以完成安裝。
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\PendingFileRenameOperations
如果下列其中一項條件成立,Exchange Analyzer 就會顯示一則錯誤訊息:
- UpdateExeVolatile 登錄機碼值為 0 以外的任何值。
- PendingFileRenameOperations 登錄機碼具有任意值。
若要解決此問題,請重新啟動系統,然後再次執行 Exchange 安裝程式。
如果系統重新啟動之後,Exchange Analyzer 仍繼續回報此錯誤,表示登錄機碼可能包含必須移除的孤立值。以下為這些機碼的可能值。
| 重要事項: |
|---|
| 這篇文章包含和編輯登錄有關的資訊。在編輯登錄之前,請確定若發生問題,您知道如何還原登錄。如需如何還原登錄的詳細資訊,請檢閱 Regedit.exe 或 Regedt32.exe 中的<還原登錄>說明主題。 |
- 開啟登錄編輯程式,例如 Regedit.exe 或 Regedt32.exe。
- 瀏覽至 HKLM\SOFTWARE\Microsoft\Updates\
- 在右瀏覽窗格中,連按兩下 UpdateExeVolatile 機碼。
- 將該機碼設定為值 0
- 關閉登錄編輯程式。
- 開啟登錄編輯程式,例如 Regedit.exe 或 Regedt32.exe。
- 瀏覽至 HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\
- 在右瀏覽窗格中的 PendingFileRenameOperations 機碼上按一下滑鼠右鍵,然後選取 [刪除]。
- 關閉登錄編輯程式。
2010年1月12日 星期二
Website Test behind the Great Firewall of China
Test any website in real-time to check if it is accessible from China. The Golden Shield Project (a.k.a. Great Firewall of China) is owned by the Government of China (MPS) and was started in 1998. The firewall system blocks website content by preventing IP addresses from being routed through and consists of standard firewall and proxy servers at the Internet gateways of China's ISPs. The banning of websites is mostly uncoordinated and ad-hoc, with some web sites being blocked from one city and the same web sites being allowed from other cities and vice versa. (You can find more details here.)
Check your website from the following cities in China: Shanghai, Beijing, Guangzhou and Hong Kong.
Check your website from the following cities in China: Shanghai, Beijing, Guangzhou and Hong Kong.
驅動人生 全方位驱动安装、升级、备份、还原等简易操作一体化
軟件名稱:驅動人生
支持系統:Windows 2000/Windows xp/Windows 2003/Windows Vista/Windows 2008/Windows 7
以上Windows系統對應32位(bit)/64位(bit)
支持系統:Windows 2000/Windows xp/Windows 2003/Windows Vista/Windows 2008/Windows 7
以上Windows系統對應32位(bit)/64位(bit)
Comodo Time Machine(免Reboot還原系統)
Why use Comodo Time Machine (CTM)?
Comodo Time Machine (CTM) is a powerful system rollback utility that allows users to quickly restore their computers to an earlier point in time. CTM 'snapshots' are a complete record of your entire system (including the registry, critical operating system files and user created documents).Layered Security
- Schedule automatic snapshots to be taken at regular intervals
- Roll back to the last known working state in the event of virus attacks or crashes
- Take snapshots of your computer before large installations or system maintenance
Comodo Time Machine features an intuitive, friendly interface which offers quick and easy access to all functionality in the application. Additionally, it also features a sub-console that can be accessed before Windows starts and a Quick Operation console containing shortcuts to important and commonly executed tasks.
Supported Operating Systems:
- Windows 7.0 (32 and 64 bit)
- Windows Vista (32 and 64 bit)
- Windows XP with service pack 2
or higher (32 and 64 bit) - Windows Server 2003
(32 and 64 bit) - Windows Server 2008
(32 and 64 bit. Except Windows Server 2008 Core)
- Intel Pentium III Processor or higher
- 128 MB RAM
NoDrives Manager
NoDrives Manager is a free, simple tool for hiding Windows logical drives by modifying the registry. The hidden drives are still accessible but they are not visible in the Windows Explorer.
2010年1月11日 星期一
使用 Ntdsutil.exe 抓取或傳輸 FSMO 角色到網域控制站
某些網域和企業的操作,是藉由 Active Directory 網域或樹系中單一網域控制站而執行,並不適合多主機的更新。而指派於執行這些特殊操作的網域控制站,則稱為操作主機或 FSMO 角色持有者。
下列清單說明在 Active Directory 樹系中的 5 種特殊 FSMO 角色,以及這些角色所執行的相依操作:
每個 FSMO 角色的磁碟分割列於下列清單中:
其中的 FSMO 角色已受到抓取的網域控制站,不得與樹系中現有的網域控制站進行通訊。在這種情況中,您必須在這類網域控制站格式化硬碟並重新安裝作業系統,或在私人網路強制將這類網域控制站降級,然後利用 ntdsutil /metadata cleanup 命令,在樹系剩下的網域控制站移除它們的中繼資料。如果繼續使用之前已經抓取到樹系中的 FSMO 角色持有者,則可能有原角色持有者照先前方式運作的風險,直到該持有者輸入複寫角色抓取的資訊為止。兩個網域控制站擁有相同的 FSMO 角色,其已知的風險包括會建立擁有 RID 集區重疊和其他問題的安全性原則。
下列清單說明在 Active Directory 樹系中的 5 種特殊 FSMO 角色,以及這些角色所執行的相依操作:
- 架構主機 - 架構主機角色範圍涵蓋整個樹系,每個樹系都有一個架構主機角色。您必須有這個角色才能擴充 Active Directory 樹系的架構,或執行 adprep /domainprep 命令。
- 網域命名主機 - 網域命名主機角色範圍涵蓋整個樹系,每個樹系都有一個網域命名主機角色。您必須有這個角色才能將網域或應用程式磁碟分割新增到樹系 (或從樹系移除)。
- RID 主機 - RID 主機角色範圍涵蓋整個網域,每個網域都有一個 RID 主機角色。您必須有這個角色才能配置 RID 集區,讓新的或現有的網域控制站能建立使用者帳戶、電腦帳戶或安全性群組。
- PDC 模擬器 - PDC 模擬器角色範圍涵蓋整個網域,每個網域都有一個 PDC 模擬器角色。您必須有這個角色,才能讓網域控制站將資料庫更新傳送到 Windows NT 備份網域控制站。此外,擁有該角色的網域控制站也會被特定的管理工具以及使用者帳戶與電腦帳戶密碼的更新鎖定。
- 基礎結構主機 - 基礎結構主機角色範圍涵蓋整個網域,每個網域都有一個基礎結構主機角色。 您必須擁有這個角色,才能讓網域控制站順利執行 adprep /forestprep 命令,並且更新 SID 屬性和各網域參照物件的辨別名稱屬性。
- 系統管理員以 GUI 系統管理工具重新指派角色。
- 系統管理員以 ntdsutil /roles 命令重新指派角色。
- 系統管理員以 Active Directory 安裝精靈,緩和地將持有角色的網域控制站降級。該精靈會將所有本機持有的角色重新指派給樹系中現有的網域控制站。利用 dcpromo /forceremoval 命令所執行的降級,會讓 FSMO 角色處於無效的狀態,直到系統管理員重新指派角色為止。
- 目前的角色持有者可以正常操作,並且可供新的 FSMO 擁有者透過網路存取。
- 您正緩和地將網域控制站降級,該控制站目前擁有您要指派給 Active Directory 樹系中,特定網域控制站的 FSMO 角色。
- 目前擁有 FSMO 角色的網域控制站將要離線以進行排定維護,而您需要特定的 FSMO 角色以指派給「現用」網域控制站。這可能需要執行與 FSMO 擁有者進行連線的作業。尤其是 PDC 模擬器角色特別符合這種情形,而 RID 主機角色、網域命名主機角色和架構主機角色則比較不一定。
- 目前的角色持有者正發生操作上的錯誤,此錯誤讓 FSMO 相依操作無法順利完成,且無法傳輸該角色。
- 利用 dcpromo /forceremoval 命令,強制將擁有 FSMO 角色的網域控制站降級。
- 原本擁有特定角色的電腦之作業系統已不存在,或是已重新安裝。
每個 FSMO 角色的磁碟分割列於下列清單中:
摺疊此表格展開此表格
| FSMO 角色 | 磁碟分割 |
| 架構 | CN=Schema,CN=configuration,DC=<樹系根網域> |
| 網域命名主機 | CN=configuration,DC=<樹系根網域> |
| PDC | DC=<網域> |
| RID | DC=<網域> |
| 基礎結構 | DC=<網域> |
其中的 FSMO 角色已受到抓取的網域控制站,不得與樹系中現有的網域控制站進行通訊。在這種情況中,您必須在這類網域控制站格式化硬碟並重新安裝作業系統,或在私人網路強制將這類網域控制站降級,然後利用 ntdsutil /metadata cleanup 命令,在樹系剩下的網域控制站移除它們的中繼資料。如果繼續使用之前已經抓取到樹系中的 FSMO 角色持有者,則可能有原角色持有者照先前方式運作的風險,直到該持有者輸入複寫角色抓取的資訊為止。兩個網域控制站擁有相同的 FSMO 角色,其已知的風險包括會建立擁有 RID 集區重疊和其他問題的安全性原則。
傳輸 FSMO 角色
如果要使用 Ntdsutil 公用程式傳輸 FSMO 角色,請執行下列步驟:- 登入 Windows 2000 Server 或 Windows Server 2003 成員電腦或樹系 (要傳輸 FSMO 角色的地方) 中的網域控制站。建議您登入要指派 FSMO 角色的網域控制站。登入的使用者必須是要傳輸架構主機,或網域命名主機角色的企業系統管理員群組成員;或正要傳輸 PDC 模擬器、RID 主機和基礎結構主機等角色,其所在網域的網域系統管理員群組之成員。
- 按一下 [開始],按一下 [執行],在 [開啟] 方塊中輸入 ntdsutil,然後按一下 [確定]。
- 輸入 roles,再按下 ENTER。
注意 如果要在 Ntdsutil 公用程式所有提示字元中,查看可用的命令清單,請輸入 ?,然後按下 ENTER。 - 輸入 connections,再按下 ENTER。
- 輸入 connect to server servername,然後按 ENTER,其中 servername 是您要指派 FSMO 角色的網域控制站之名稱。
- 在 server connections 提示字元中輸入 q,然後按下 ENTER。
- 輸入 transfer role,其中 role 是您要傳輸的角色。如需可以傳送的角色之清單,請在 fsmo maintenance 提示字元中輸入 ?,然後按下 ENTER;或直接查看本文件開頭所列的角色清單。例如,如果要傳輸 RID 主機角色,請輸入 transfer rid master。唯一的例外是 PDC 模擬器角色,該角色的語法是 transfer pdc,並非 transfer pdc emulator。
- 請在 fsmo maintenance 提示字元中輸入 q,然後按下 ENTER,獲得存取 ntdsutil 提示字元的權限。輸入 q,然後按下 ENTER,結束 Ntdsutil 公用程式。
抓取 FSMO 角色
如果要使用 Ntdsutil 公用程式抓取 FSMO 角色,請執行下列步驟:- 登入 Windows 2000 Server 或 Windows Server 2003 成員電腦或樹系 (要抓取 FSMO 角色的地方) 中的網域控制站。建議您登入要指派 FSMO 角色的網域控制站。登入的使用者必須是要傳輸架構主機,或網域命名主機角色的企業系統管理員群組成員;或正要傳輸 PDC 模擬器、RID 主機和基礎結構主機等角色,其所在網域的網域系統管理員群組之成員。
- 按一下 [開始],按一下 [執行],在 [開啟] 方塊中輸入 ntdsutil,然後按一下 [確定]。
- 輸入 roles,再按下 ENTER。
- 輸入 connections,再按下 ENTER。
- 輸入 connect to server servername,然後按 ENTER,其中 servername 是您要指派 FSMO 角色的網域控制站之名稱。
- 在 server connections 提示字元中輸入 q,然後按下 ENTER。
- 輸入 seize role,其中 role 是您要抓取的角色。如需可以抓取的角色之清單,請在 fsmo maintenance 提示字元中輸入 ?,然後按下 ENTER;或直接查看本文件開頭所列的角色清單。例如,如果要抓取 RID 主機角色,請輸入 seize rid master。唯一的例外是 PDC 模擬器角色,該角色的語法是 seize pdc,並非 seize pdc emulator。
- 請在 fsmo maintenance 提示字元中輸入 q,然後按下 ENTER,獲得存取 ntdsutil 提示字元的權限。輸入 q,然後按下 ENTER,結束 Ntdsutil 公用程式。
注意- 在一般情況下,這 5 種角色全都必須指派到樹系「現用」的網域控制站中。如果擁有 FSMO 角色的網域控制站已在其角色傳輸前終止服務,您必須將所有角色抓取到適當且運作正常的網域控制站中。建議您只在其他網域控制站尚未返回網域時抓取所有的角色。如果可以的話,請修復有指派 FSMO 角色的 故障網域控制站。您必須決定要留在其餘網域控制站的角色,如此才能讓這 5 個角色都指派到單一的網域控制站。 如需有關 FSMO 角色放置的詳細資訊,請按一下下面的文件編號,檢視「Microsoft 知識庫」中的文件:223346 (http://support.microsoft.com/kb/223346/ ) 在 Windows 2000 網域控制站上安置與最佳化 FSMO
- 如果原先持有任何 FSMO 角色的網域控制站不在網域中,且已利用本文件說明的步驟抓取其中的角色,請按照下列「Microsoft 知識庫」文件說明的程序,從 Active Directory 移除該控制站:216498 (http://support.microsoft.com/kb/216498/ ) HOW TO:在網域控制站降級失敗後,移除 Active Directory 中的資料
- 使用 Windows 2000 版本或 Windows Server 2003 組建 3790 版本的 ntdsutil /metadata cleanup 命令移除網域控制站的中繼資料,並不會將指定到現用網域控制站的 FSMO 角色重新定位。Windows Server 2003 Service Pack 1 (SP1) 版本的 Ntdsutil 公用程式會自動化這個工作,並且移除網域控制站中繼資料的額外元素。
- 某些客戶比較喜歡不還原 FSMO 角色持有者的系統狀態備份,以避免在建立備份後發生角色已經重新指派的情況。
- 請勿將基礎結構主機角色放置在與通用類別目錄伺服器相同的網域控制站上。如果基礎結構主機是在通用類別目錄伺服器上執行,則會停止更新物件資訊,因為它不包含本身不持有之物件的參照。這是因為通用類別目錄伺服器會保留樹系中每個物件的部分複本。
- 在一般情況下,這 5 種角色全都必須指派到樹系「現用」的網域控制站中。如果擁有 FSMO 角色的網域控制站已在其角色傳輸前終止服務,您必須將所有角色抓取到適當且運作正常的網域控制站中。建議您只在其他網域控制站尚未返回網域時抓取所有的角色。如果可以的話,請修復有指派 FSMO 角色的 故障網域控制站。您必須決定要留在其餘網域控制站的角色,如此才能讓這 5 個角色都指派到單一的網域控制站。 如需有關 FSMO 角色放置的詳細資訊,請按一下下面的文件編號,檢視「Microsoft 知識庫」中的文件:
- 按一下 [開始],依序指向 [程式集] 及 [系統管理工具],再按一下 [Active Directory 站台及服務]。
- 按兩下左側窗格中的 [站台],然後找到適當的站台;如果沒有其他可用的站台,請按一下 [Default-first-site-name]。
- 開啟「伺服器」資料夾,然後按一下網域控制站。
- 在網域控制站的資料夾中,按兩下 [NTDS 設定]。
- 在 [執行] 功能表上,按一下 [內容]。
- 在 [一般] 索引標籤上,檢視 [通用類別目錄] 核取方塊,確認是否已選取。
2010年1月10日 星期日
Windows Core Configurator 2.0 (Windows Server 2008 R2)
Core Configurator 2.0
We are pleased to announce the latest version of Core Configurator built and designed for Windows Server 2008 R2 Core edition!
It is completely open source so it can be amended and change to fit your requirements, this version has been a year in the making and has been written in powershell with a reference to Winforms so that a GUI format is displayed.
The primary focus of this project is to try and get feedback and contributions back from the community to make this a tool the best/ free tool everyone will want in there toolkit, so if you have some code or features that you might want included then please leave a comment and we will get in touch.
Core Configuration tasks include:
- Product Licensing
- Networking Features
- DCPromo Tool
- ISCSI Settings
- Server Roles and Features
- User and Group Permissions
- Share Creation and Deletion
- Dynamic Firewall settings
- Display | Screensaver Settings
- Add & Remove Drivers
- Proxy settings
- Windows Updates (Including WSUS)
- Multipath I/O
- Hyper-V including virtual machine thumbnails
- JoinDomain and Computer rename
- Add/remove programs
- Services
- WinRM
- Complete logging of all commands executed
Please Download the latest release and run Start_CoreConfig.wsf
If you require the previous release for Windows Server 2008 R1 then please see the download section for Core Configurator 1.1 as Core Configurator 2.0 requires Powershell 2.0 and NetFx..
Please can you rate and review as this really helps us gather information and feedback...
Last edited Dec 4 2009 at 9:53 PM by CoreConfigTeam, version 22
How to Add an SPF Record in Windows 2000 and Windows 2003 DNS
Step 1: Select and open the domain in which you wish to add the SPF record. Right-click in the record list and select "Other New Records..." from the menu.
| |||||||||
2010年1月7日 星期四
限制訪問與AppLocker程序在Windows 7
使用AppLocker
To access Group Policy Editor and create rules in AppLocker you'll need to be logged in as Administrator.要訪問組策略編輯器,創造規則AppLocker您需要先登錄作為管理員。 Click on Start and type gpedit.msc into the search box and hit Enter.單擊開始, 鍵入 gpedit.msc到搜索框中並按下回車鍵。

Under Local Computer Policy go to Computer Configuration \ Windows Settings \ Security Settings \ Application Control Policies \ AppLocker.在本地計算機策略計算機配置\ Windows設置\安全設置\應用控制策略\ AppLocker。

Now you will see the overall controls for the applications.現在,你將看到的整體控制的應用。

Under Configure Rule Enforcement click on the Configure rule enforcement link.根據配置規則執行單擊配置規則的執行環節。

Now under AppLocker Properties check the boxes next to Configured under Executable rules then click Ok.現在,檢查下AppLocker屬性旁邊的框下的可執行文件的規則配置 ,然後單擊確定。

Blocking Apps from Running 阻止應用程序的運行
In this scenario, Jack wastes time playing games like Minesweeper and Solitaire when he should be doing his homework, so we are going to block all of the games.在這種情況下,傑克浪費時間玩遊戲像掃雷和紙牌遊戲的時候他應該做的功課,因此我們要阻止所有的遊戲。 After completing the steps above, under the Overview section click on Executable Rules.在完成上述步驟,在概述部分點擊可執行規則。

Since this is your first time accessing AppLocker, there will be no rules listed.由於這是您第一次訪問AppLocker,就沒有規則列出。 Right-click and select Create New Rule…右擊並選擇創建新規則...

This opens up the Create Executable Rules wizard and you can select not to show the introduction screen at start up for the next time you access it.這開闢了創建可執行規則嚮導,您可以選擇不顯示屏幕上介紹的啟動下一次訪問。

Select Permissions under Action select Deny.選擇權限下的行動選擇拒絕。

Add the user you want to block, in this case it's Jack.將用戶添加要阻止,在這種情況下,它的傑克。

After you've selected the deny action and selected the user continue to the next step.當你選擇了否定行動,並選擇用戶繼續下一個步驟。

In Conditions you can select from Publisher, Path or File hash.在條件您可以選擇從Publisher,路徑或文件哈希。 We don't want Jack to have access to any of the games.我們不希望傑克能夠獲得任何遊戲。 so we will select Path.所以我們會選擇路徑。

Click on Browse Folders and select the Microsoft Games folder.點擊瀏覽文件夾並選擇Microsoft遊戲文件夾。

In the next screen you could add Exceptions like allowing certain files, but because we are blocking the entire games directory we'll skip to the next screen.在接下來的屏幕上,您可以添加例外諸如讓某些文件,而是因為我們正阻礙整個遊戲目錄中,我們將直接跳到下一個畫面。

Here you can add a description to the rule so you can keep track of them is there are several rules configured.在這裡您可以添加說明的規定,使您可以跟踪他們是有一些規則的配置。 When everything looks right click on Create.當一切看起來右鍵點擊創建。

A message pops up saying default rules haven't been created yet.彈出一個消息說,默認規則還沒有創建。 It is important to make sure they are created so click Yes to this message.重要的是確保它們是創造了點擊此郵件。

Now you will see the default rules and the new one you created showing Jack is denied access to the Microsoft Games directory.現在你會看到默認的規則和新的創建,顯示傑克被拒絕訪問Microsoft遊戲目錄。

After creating the rule make sure and go into services and make Application Identification is started and that it's set to automatically start as well otherwise the rules won't work.在創建規則進行確認並進入應用服務,使鑑定啟動,它的設置為自動啟動,以及規則,否則將無法工作。 By default this service is not started so you will need to enable it.默認情況下此服務未啟動,因此您將需要啟用它。
![sshot - 2009 - 11 - 08 - [22-52-10] sshot-2009-11-08-[22-52-10]](http://www.howtogeek.com/wp-content/uploads/2009/11/sshot20091108225210.png)
Now, when Jack logs into his user account and tries to access the games he will only see the following message.現在,當傑克登錄到他的用戶帳戶,並嘗試訪問比賽,他將只能看到下面的消息。 Only an Administrator can go in and change the rule.只有管理員可以進入並改變規則。

Conclusion 結論
Use caution when configuring the rules and only start the Application Identity service after everything looks right.使用時要小心配置的規則,只有啟動應用程序標識服務在萬象的權利。 Otherwise you have the potential of locking yourself out of all applications including AppLocker.AppLocker is a powerful feature included in Windows 7 and we showed you a basic rule so you can get an idea of how it works.否則,你有可能自己把自己鎖定的所有應用,包括AppLocker.AppLocker是一個強大的功能包含在Windows 7,我們發現您的基本規則,您可以得到一個想法它如何工作。 In the future we'll take a look at more complex tasks to accomplish and gain tight control over what programs each user is able to access.在未來,我們將看看在更複雜的任務要完成,並取得嚴格控制哪些程序每個用戶能夠訪問。
To access Group Policy Editor and create rules in AppLocker you'll need to be logged in as Administrator.要訪問組策略編輯器,創造規則AppLocker您需要先登錄作為管理員。 Click on Start and type gpedit.msc into the search box and hit Enter.單擊開始, 鍵入 gpedit.msc到搜索框中並按下回車鍵。

Under Local Computer Policy go to Computer Configuration \ Windows Settings \ Security Settings \ Application Control Policies \ AppLocker.在本地計算機策略計算機配置\ Windows設置\安全設置\應用控制策略\ AppLocker。

Now you will see the overall controls for the applications.現在,你將看到的整體控制的應用。

Under Configure Rule Enforcement click on the Configure rule enforcement link.根據配置規則執行單擊配置規則的執行環節。

Now under AppLocker Properties check the boxes next to Configured under Executable rules then click Ok.現在,檢查下AppLocker屬性旁邊的框下的可執行文件的規則配置 ,然後單擊確定。

Blocking Apps from Running 阻止應用程序的運行
In this scenario, Jack wastes time playing games like Minesweeper and Solitaire when he should be doing his homework, so we are going to block all of the games.在這種情況下,傑克浪費時間玩遊戲像掃雷和紙牌遊戲的時候他應該做的功課,因此我們要阻止所有的遊戲。 After completing the steps above, under the Overview section click on Executable Rules.在完成上述步驟,在概述部分點擊可執行規則。

Since this is your first time accessing AppLocker, there will be no rules listed.由於這是您第一次訪問AppLocker,就沒有規則列出。 Right-click and select Create New Rule…右擊並選擇創建新規則...

This opens up the Create Executable Rules wizard and you can select not to show the introduction screen at start up for the next time you access it.這開闢了創建可執行規則嚮導,您可以選擇不顯示屏幕上介紹的啟動下一次訪問。

Select Permissions under Action select Deny.選擇權限下的行動選擇拒絕。

Add the user you want to block, in this case it's Jack.將用戶添加要阻止,在這種情況下,它的傑克。

After you've selected the deny action and selected the user continue to the next step.當你選擇了否定行動,並選擇用戶繼續下一個步驟。

In Conditions you can select from Publisher, Path or File hash.在條件您可以選擇從Publisher,路徑或文件哈希。 We don't want Jack to have access to any of the games.我們不希望傑克能夠獲得任何遊戲。 so we will select Path.所以我們會選擇路徑。

Click on Browse Folders and select the Microsoft Games folder.點擊瀏覽文件夾並選擇Microsoft遊戲文件夾。

In the next screen you could add Exceptions like allowing certain files, but because we are blocking the entire games directory we'll skip to the next screen.在接下來的屏幕上,您可以添加例外諸如讓某些文件,而是因為我們正阻礙整個遊戲目錄中,我們將直接跳到下一個畫面。

Here you can add a description to the rule so you can keep track of them is there are several rules configured.在這裡您可以添加說明的規定,使您可以跟踪他們是有一些規則的配置。 When everything looks right click on Create.當一切看起來右鍵點擊創建。

A message pops up saying default rules haven't been created yet.彈出一個消息說,默認規則還沒有創建。 It is important to make sure they are created so click Yes to this message.重要的是確保它們是創造了點擊此郵件。

Now you will see the default rules and the new one you created showing Jack is denied access to the Microsoft Games directory.現在你會看到默認的規則和新的創建,顯示傑克被拒絕訪問Microsoft遊戲目錄。

After creating the rule make sure and go into services and make Application Identification is started and that it's set to automatically start as well otherwise the rules won't work.在創建規則進行確認並進入應用服務,使鑑定啟動,它的設置為自動啟動,以及規則,否則將無法工作。 By default this service is not started so you will need to enable it.默認情況下此服務未啟動,因此您將需要啟用它。
![sshot - 2009 - 11 - 08 - [22-52-10] sshot-2009-11-08-[22-52-10]](http://www.howtogeek.com/wp-content/uploads/2009/11/sshot20091108225210.png)
Now, when Jack logs into his user account and tries to access the games he will only see the following message.現在,當傑克登錄到他的用戶帳戶,並嘗試訪問比賽,他將只能看到下面的消息。 Only an Administrator can go in and change the rule.只有管理員可以進入並改變規則。

Conclusion 結論
Use caution when configuring the rules and only start the Application Identity service after everything looks right.使用時要小心配置的規則,只有啟動應用程序標識服務在萬象的權利。 Otherwise you have the potential of locking yourself out of all applications including AppLocker.AppLocker is a powerful feature included in Windows 7 and we showed you a basic rule so you can get an idea of how it works.否則,你有可能自己把自己鎖定的所有應用,包括AppLocker.AppLocker是一個強大的功能包含在Windows 7,我們發現您的基本規則,您可以得到一個想法它如何工作。 In the future we'll take a look at more complex tasks to accomplish and gain tight control over what programs each user is able to access.在未來,我們將看看在更複雜的任務要完成,並取得嚴格控制哪些程序每個用戶能夠訪問。
「 尋找 」 和 「 還原已刪除 AD 物件
ADRecycleBin
overall.ca
曾經被四處移動快速而管理或清潔向上 Active Directory (AD) 網域,並刪除您不可以擁有的項目嗎? 或者,或許您是擔心新 staffer 了能夠從目錄中刪除物件。
讓我們面對它:發生錯誤即使有了所有這些確認對話方塊。 Windows Server 2008 R2 新增自己 Active Directory 資源回收筒] 功能,但是如果您還沒有被還,升級您的網域,或是您想要管理這項新功能的替代方法您可能想要取出總體方案 Inc.的免費工具,ADRecycleBin。
這個簡易用公用程式會是可執行檔,一個單一 500 KB,讓您可以新增它到管理 USB 金鑰或 CD,如此就會很方便,不論您的所在位置。 然後,當您從 AD 中刪除物件時它不會真的取得刪除 ; 而,isDeleted"屬性是集和它的移到特殊的 CN 呼叫已刪除物件。 這些物件稱為 「 刪除記錄。
工具抓取這些標記,並可讓您一次還原一系列。 當您載入 ADRecycleBin 時,它連接至網域控制站,並顯示目前的樹系功能層級、 網域功能層級、 目前的網域以及是可使用什麼類型的 RecycleBin 功能。 Windows Server 2008 R2 您可以將繫結到 Active Directory 資源回收筒 ; 對於較早版本您可以 「 re-animate"刪除的物件。
您也可以篩選您要載入具有三個核取方塊的物件的型別:使用者和電腦、 群組,及其他。 按 一下 [載入已刪除物件上不會只是什麼您應該猜得出來 ; 載入您的刪除記錄集後您可以按一下以查看該物件包括 sAMAccountName、 SID、 CN、 lastKnownParent 和還有其他的 whenChanged 的詳細的屬性檢視的個別 AD 物件上。 下一個、 只選取您想還原並按一下 [還原已檢查的物件項的目。
ADRecycleBin 是管理您不慎刪除的 AD 物件--和絕對價值考量為 IT 工具箱的加法的簡單、 簡單又免費的方式。
價格:免費。

2010年1月6日 星期三
Windows 7還有更多「上帝模式」
對Windows 7「上帝模式」(GodMode)感到好奇的讀者,也許想知道,這個作業系統中還有很多其他類似的捷徑。
微軟的Windows部門主管對ZDNET表示,部落客發現的所謂「上帝模式」設定檔案夾,只是Windows系統中許多沒有特別說明的開發者功能之一。這類捷徑早在Vista之前就存在,目的是讓開發者更容易控制各種內部設定。
Windows部門總裁Steven Sinofsky接受本站電訪時表示,還有幾個類似、未明示的功能,可直接進入所有類型的設定,從位置選擇、電力管理,到確認生物辨識感應器等。
如同部落客發現的上帝模式,你也可以用任何名稱創造新的檔案夾,再加上特定的字串,就能直接進入各種設定的控制面板。Sinofsky表示,除了包含所有設定的上帝模式檔案夾選項,還有十多個字串,可分別創造出特定的設定檔案夾。
Sinofsky表示,「上帝模式」是部落客取的名稱,微軟內部並非以此稱呼這項功能。雖然微軟有很多這類未說明的開發者指令,它們只是複製作業系統的控制台設定。
過去幾版Windows都有這類捷徑,部落客發現的「上帝模式」也存在Windows Vista。但部分64位元版Vista使用者表示,啟用上帝模式檔案夾,會造成系統當機。微軟也說他們尚未重建該問題,但幾位讀者曾表示,他們也碰到問題。
微軟總部人員對上帝模式引起如此大的注意感到意外,並決定好好玩一玩。Sinofsky也提供本站其他可創造特別檔案夾的指令字串。但有鑑於Vista的種種問題,我建議用Windows 7電腦試驗。先用任何名稱創造一個新資料夾,然後打上句號,再加入下列任一字串。
例如:"thankscnet.{00C6D95F-329C-409a-81D7-C46C66EA7F33}" (最外側的兩個引用符號不算)
微軟提供的字串如下:
{00C6D95F-329C-409a-81D7-C46C66EA7F33}
{0142e4d0-fb7a-11dc-ba4a-000ffe7ab428}
{025A5937-A6BE-4686-A844-36FE4BEC8B6D}
{05d7b0f4-2121-4eff-bf6b-ed3f69b894d9}
{1206F5F1-0569-412C-8FEC-3204630DFB70}
{15eae92e-f17a-4431-9f28-805e482dafd4}
{17cd9488-1228-4b2f-88ce-4298e93e0966}
{1D2680C9-0E2A-469d-B787-065558BC7D43}
{1FA9085F-25A2-489B-85D4-86326EEDCD87}
{208D2C60-3AEA-1069-A2D7-08002B30309D}
{20D04FE0-3AEA-1069-A2D8-08002B30309D}
{2227A280-3AEA-1069-A2DE-08002B30309D}
{241D7C96-F8BF-4F85-B01F-E2B043341A4B}
{4026492F-2F69-46B8-B9BF-5654FC07E423}
{62D8ED13-C9D0-4CE8-A914-47DD628FB1B0}
{78F3955E-3B90-4184-BD14-5397C15F1EFC}
提醒各位,要創造上帝模式資料夾,請使用這個字串:
{ED7BA470-8E54-465E-825C-99712043E01C}
微軟的Windows部門主管對ZDNET表示,部落客發現的所謂「上帝模式」設定檔案夾,只是Windows系統中許多沒有特別說明的開發者功能之一。這類捷徑早在Vista之前就存在,目的是讓開發者更容易控制各種內部設定。
Windows部門總裁Steven Sinofsky接受本站電訪時表示,還有幾個類似、未明示的功能,可直接進入所有類型的設定,從位置選擇、電力管理,到確認生物辨識感應器等。
如同部落客發現的上帝模式,你也可以用任何名稱創造新的檔案夾,再加上特定的字串,就能直接進入各種設定的控制面板。Sinofsky表示,除了包含所有設定的上帝模式檔案夾選項,還有十多個字串,可分別創造出特定的設定檔案夾。
Sinofsky表示,「上帝模式」是部落客取的名稱,微軟內部並非以此稱呼這項功能。雖然微軟有很多這類未說明的開發者指令,它們只是複製作業系統的控制台設定。
過去幾版Windows都有這類捷徑,部落客發現的「上帝模式」也存在Windows Vista。但部分64位元版Vista使用者表示,啟用上帝模式檔案夾,會造成系統當機。微軟也說他們尚未重建該問題,但幾位讀者曾表示,他們也碰到問題。
微軟總部人員對上帝模式引起如此大的注意感到意外,並決定好好玩一玩。Sinofsky也提供本站其他可創造特別檔案夾的指令字串。但有鑑於Vista的種種問題,我建議用Windows 7電腦試驗。先用任何名稱創造一個新資料夾,然後打上句號,再加入下列任一字串。
例如:"thankscnet.{00C6D95F-329C-409a-81D7-C46C66EA7F33}" (最外側的兩個引用符號不算)
微軟提供的字串如下:
{00C6D95F-329C-409a-81D7-C46C66EA7F33}
{0142e4d0-fb7a-11dc-ba4a-000ffe7ab428}
{025A5937-A6BE-4686-A844-36FE4BEC8B6D}
{05d7b0f4-2121-4eff-bf6b-ed3f69b894d9}
{1206F5F1-0569-412C-8FEC-3204630DFB70}
{15eae92e-f17a-4431-9f28-805e482dafd4}
{17cd9488-1228-4b2f-88ce-4298e93e0966}
{1D2680C9-0E2A-469d-B787-065558BC7D43}
{1FA9085F-25A2-489B-85D4-86326EEDCD87}
{208D2C60-3AEA-1069-A2D7-08002B30309D}
{20D04FE0-3AEA-1069-A2D8-08002B30309D}
{2227A280-3AEA-1069-A2DE-08002B30309D}
{241D7C96-F8BF-4F85-B01F-E2B043341A4B}
{4026492F-2F69-46B8-B9BF-5654FC07E423}
{62D8ED13-C9D0-4CE8-A914-47DD628FB1B0}
{78F3955E-3B90-4184-BD14-5397C15F1EFC}
提醒各位,要創造上帝模式資料夾,請使用這個字串:
{ED7BA470-8E54-465E-825C-99712043E01C}
2010年1月5日 星期二
Freeware background removing program
InstantMask
Instant Mask is a quick and simple to use freeware background removing program.See description below (or video demo here) to see how it works :
1. Open a picture you want to edit

2. Mark the areas of foreground and background

3. Press preview to see you changes

4. If nescessary add more marks and save the image.
Download InstantMask.
We also have a more advanced background removing tool InstantMask Pro.
Check the link above to see many additional features it can offer.
Windows 7 設定
修復右鍵選單項目:
"HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers" 找任何你不要題示的項目前加"-"
防止Windows Update自動重開機:
"HKEY_LOCAL_MACHINE\SOFTWARE\Polices\Microsft\Windows\WindowsUpdate\AU",新增32 bit DWORD值"NoAutoRebootWithLoggedOn Users" 數值為1
自動登入教學:
RUN>netplwiz
"HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers" 找任何你不要題示的項目前加"-"
防止Windows Update自動重開機:
"HKEY_LOCAL_MACHINE\SOFTWARE\Polices\Microsft\Windows\WindowsUpdate\AU",新增32 bit DWORD值"NoAutoRebootWithLoggedOn Users" 數值為1
自動登入教學:
RUN>netplwiz
eXtreme Power Supply Calculator Lite v2.5
eXtreme Power Supply Calculator v2.5
 | Many people often overlook the importance of Amperage and its impact on their computers. You can find different types of Power Supplies on the market that supply more then enough Wattage to run your system. However, many of them lack Amperage, which is necessary to back offered Wattage up. Therefore, it is important that you know exactly how many Amperes your system needs in order to work properly, without PSU causing any problems or even damage to computer components. The eXtreme Power Supply Calculator Pro contains such necessary Amperage data. |
訂閱:
文章 (Atom)
 回此頁最上方
回此頁最上方


