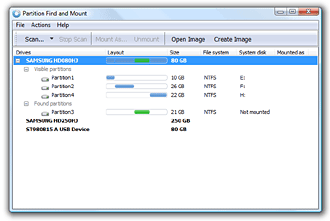
Partition Find & Mount is:
- Easy to use. You do not need special knowledge to use the software.
- Safe to your data. There is no possible way you could get things worse.
- Free for personal use. Use it as much as you like.
 |
|
 |
|









 |  |
 | |
 * Resizes your photos to your digital photo frame’s native resolution.
* Resizes your photos to your digital photo frame’s native resolution.
PDF Password Remover Tool | ||
 | PDF Password Remover tool is a simple tool that can be used to decrypt password protected PDF files which have their "owner" password set. PDF files with the owner password set would prevent viewers from editing, selecting text, printing and otherwise changing any of the pdf properties such as form fields etc. This PDF Password Remover tool will decrypt and remove owner passwords from any PDF document. The Password Remover tool will NOT work with PDF files that have a "user password" set. Please use this tool to remove passwords from PDF files that belong to you. It was developed to help you recover PDF files in cases where you forget the owner passwords you once set and can no longer remember. It can be life-saving when you misplace your originals. Best of all, we provide this wonderful tool absolutely free for personal use. Download the Free PDF Password Remover Tool | |
 All you need is to install the «manager» part on your computer and the «employee» part on each computer you want to monitor. After this, you will be able to control all the computer screens and office through webcams in real time and off-line modes. The program can capture either entire desktops or only active applications (up to 250 employees per each manager station !!!). You can record voice via microphones and then play any mp3 audio file anytime.
All you need is to install the «manager» part on your computer and the «employee» part on each computer you want to monitor. After this, you will be able to control all the computer screens and office through webcams in real time and off-line modes. The program can capture either entire desktops or only active applications (up to 250 employees per each manager station !!!). You can record voice via microphones and then play any mp3 audio file anytime. The off-line work time counter allows to see all statistic information about work time of any employee.
The off-line work time counter allows to see all statistic information about work time of any employee.